SIGMA Rules
Struggling to remember the ever-changing query syntax across different SIEM platforms? You’re not alone! Every tool—Splunk, Elastic, Sentinel—has its own scripting language, making threat detection a challenge.
But don’t worry—SIGMA rules are here to save the day! 🚀
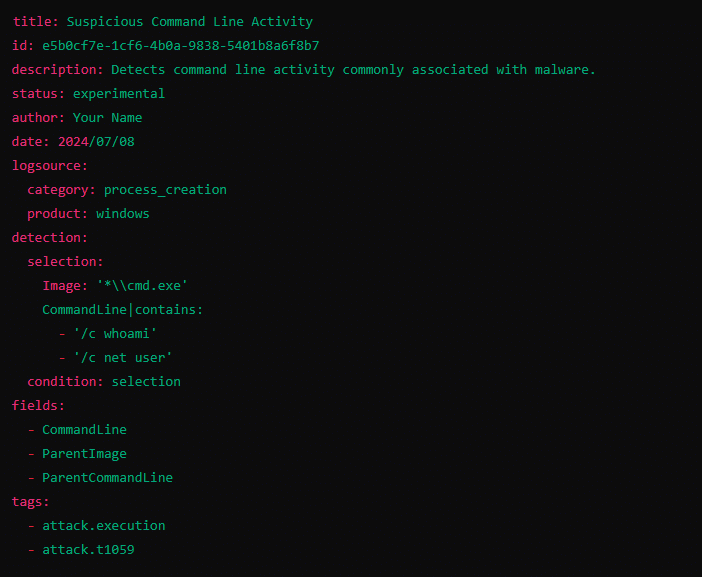
SIGMA is the Swiss knife of writing detection queries in SIEM, you write a single detection rule and convert it into queries for your favourite SIEM tool. No more memorizing multiple syntaxes—just write once and translate as needed.
Want to detect BloodHound in your environment?
Here’s my git repository for an example of a SIGMA rule in action: Threat Detection
Threat detection just got easier! Are you using SIGMA in your SOC? Let me know your thoughts!